Gatekeeping Theory
Gatekeeping theory, conceptualized by Kurt Lewin in 1943, describes the process in which unnecessary information is blocked and filtered through the use of a metaphorical "gate." Those who act as "gatekeepers" decide as to what information should and should not be publicized. One example of a gatekeeper is a news editor. Those who act as news editors are tasked with figuring out what news is relevant enough to be published. Each day, several note-worthy events occur, however, it is impossible for all of them to be covered. Therefore, gatekeeping plays a vital role in media. Gatekeeping is different than censorship, in that it has to do with maintaining relevant information. Censorship, on the other hand, deliberately removes unwanted information.
Factors of Gatekeeping
(1) Individual: The "force" at the gate, they have the most influence over what is being released. This includes the journalist who makes the report.
(2) Routine: The themes shown in the media are always in a pattern. News sources typically have schedules for when subjects within a certain category should be publicized.
(3) Organization: Media organizations have their own narratives they want to portray, all of them have their own views, opinions, and biases. The organizations hire the journalists (the gatekeepers) and make the rules.
(4) Extra-Media: Many media outlets are governed by related people/institutions who have a say in what is published (i.e. sponsors, advertisers, government, etc). Financial supporters highly influence media companies, therefore, negative news will not intentionally pass through the gate.
(5) Ideology: The media must follow societal ideologies to maintain relevancy. Ideologies change over time, so it is important that the media respects social norms.
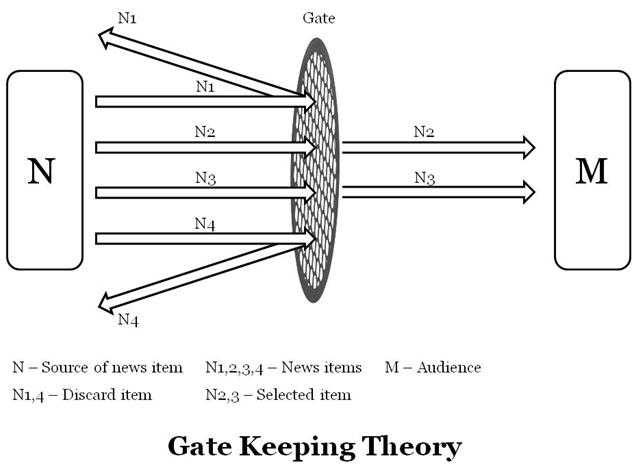 |
| Model of Gate Keeping Theory |